CSAM WEEK 1:
Cybersecurity Fundamentals and the User’s Role
Let’s face it—cybersecurity can feel like one of those techy topics that’s not really your job unless you work in IT or regularly tape up the bridge of your glasses. But if you’re part of a human services organization, protecting sensitive data is really everyone’s responsibility. You might not be building firewalls or monitoring network traffic, but the little things you do every day can either help keep information safe or leave the door open for cybercriminals. In today’s world, data is the new gold. And with the types of data we handle—like personal details, financial information, and health records—it’s crucial that we all get on board with good cybersecurity practices. After all, protecting the personal information of vulnerable populations is a responsibility we ALL share.
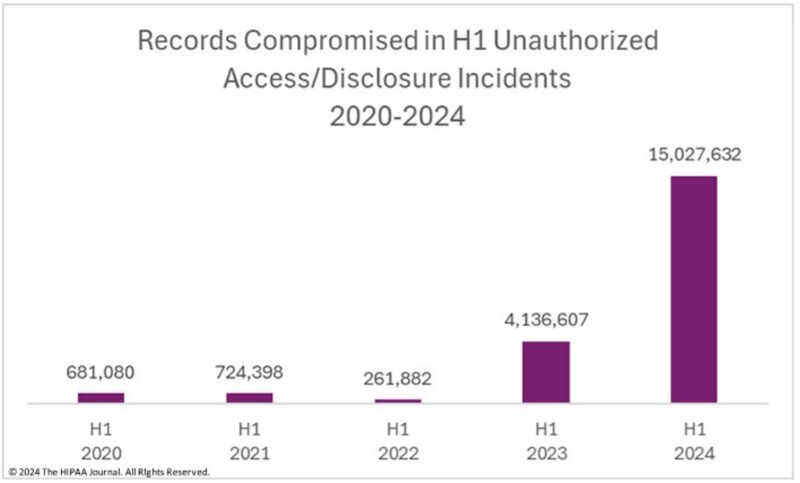 Here’s another reality check: in a digital, connected world, data is the new gold. According to the HIPAA Journal[1], 2024 has already been a record-breaking year in data breaches. And it’s not just the number of records stolen, it’s also how much it’s costing the industry. The Change Healthcare ransomware attack alone cost somewhere between $2.3 to 2.45 billion[2] (feel free to hold your pinkie to your mouth as you read that number). Even more important than money, these attacks are interfering with our ability to provide healthcare services and it’s killing patients[3]. This is serious stuff, and it’s only been getting worse.
Here’s another reality check: in a digital, connected world, data is the new gold. According to the HIPAA Journal[1], 2024 has already been a record-breaking year in data breaches. And it’s not just the number of records stolen, it’s also how much it’s costing the industry. The Change Healthcare ransomware attack alone cost somewhere between $2.3 to 2.45 billion[2] (feel free to hold your pinkie to your mouth as you read that number). Even more important than money, these attacks are interfering with our ability to provide healthcare services and it’s killing patients[3]. This is serious stuff, and it’s only been getting worse.
Great, you may be thinking, “that’s just awful… but I’m not in IT, so why do I need to know about cybersecurity?” The answer is simple: Cybersecurity isn’t just about firewalls and antivirus software; it’s about daily habits, awareness, and vigilance. October just happens to be Cyber Security Awareness Month (CSAM), so let’s kick it off by breaking down the fundamentals of cybersecurity and showing how your role fits into the bigger picture.
Why Cybersecurity Should Be on Your Radar
In a human services organization, we deal with some of the most vulnerable populations. Think about the types of information you work with daily—client case files, health records, sensitive financial information, and even details about children or people in crisis. Now imagine if that data fell into the wrong hands. Not only would it be a privacy nightmare for clients, but it could also put them at risk for identity theft, fraud, or worse.
Cybercriminals know this, and unfortunately, they target organizations like yours because they know (as we saw earlier) we handle valuable data[4]. We might not have the huge cybersecurity budgets that major corporations have, but that doesn’t mean we’re off the hook. Cybersecurity isn’t just about fancy software; it’s about creating a culture of awareness and vigilance. And that’s where you come in.
Cybersecurity 101: The Basics Everyone Should Know
Let’s start with the basics—cybersecurity is all about protecting systems, networks, and data from digital attacks. Cyberattacks are often aimed at stealing sensitive information, messing with systems, or demanding ransom money. It’s like having a house with valuables inside: you wouldn’t leave the door wide open, right? The same idea applies to the digital world.
Here are three big concepts to know:
Confidentiality:
Only authorized people should have access to certain information. If you’re not supposed to see it, don’t go looking for it. Whether it’s client data or internal files, protecting confidentiality is key.
Integrity:
This means keeping information accurate and unaltered. If someone were to change data—whether by mistake or on purpose—it could mess up everything from client care plans to financial reports.
Availability:
Authorized users need access to the information and systems when they need them. Downtime from cyberattacks can slow down your work or even stop it completely, affecting client services.
These three concepts—Confidentiality, Integrity, and Availability—make up what’s called the CIA triad. It’s like the foundation of cybersecurity, guiding how we protect the important information we handle every day.
The Cyber Threats You Should Know About
The digital world can be a dangerous place, and cybercriminals are always looking for ways to exploit vulnerabilities. Here are some common threats you should keep an eye on:
Phishing:
Ever get an email that looks legitimate but something feels off? That could be a phishing attack. Phishing is when hackers try to trick you into sharing sensitive info, like passwords or personal details, by pretending to be someone you trust. These emails might ask you to click a link, download an attachment, or log into a fake website. Just one click on a malicious link can open the door to a cyberattack.
Malware:
Malware, or malicious software, is designed to cause harm. This could be a virus, spyware, or ransomware that gets into your system and wreaks havoc. Malware can slow down your devices, steal your data, or lock you out of your files.
Ransomware:
Ransomware is a type of malware that encrypts your data and demands payment (usually in cryptocurrency) to unlock it. And paying doesn’t guarantee you’ll get your data back. For an organization like yours, ransomware can shut down critical services and put sensitive data at risk.
Insider Threats:
Not all threats come from the outside. Sometimes, people within the organization—whether on purpose or by accident—can cause security risks. This could be someone mishandling sensitive data or unintentionally falling for a phishing scam. That’s why it’s important to stay vigilant and report anything suspicious.
Weak Passwords:
We get it—coming up with unique, strong passwords can feel like a hassle. But weak or reused passwords are like leaving your front door unlocked. Cybercriminals love to exploit easy-to-guess passwords, so make sure yours are strong and varied.
Be Phishing-Savvy:
Phishing is one of the most common ways hackers gain access to systems. Always be cautious when you get unexpected emails— especially if they ask for sensitive information or seem too good to be true. Check the sender’s email address carefully, and if you’re unsure, don’t click on any links or download attachments. When in doubt, report it to your IT team. We’ll discuss this more in our week 2 blog.
Keep Safe when Web Surfing or on Your Mobile Device:
It’s easy to get into the zone when you’re web surfing and following links (or just getting lost in your stream of consciousness). Let’s be honest: the internet and global connectivity is so commonplace now it is taken for granted (even though this would seem like blue sky science fiction just a few decades ago). The bad guys know this and want to take advantage of you not paying attention (which is even easier when we get on our mobile devices). In CSAM week 3, we’ll publish another blog that helps you do that more safely.
Use Strong Passwords:
We know it’s tempting to use the same password for everything, but don’t. Instead, use strong, unique passwords for all your accounts. Make them long, with a mix of letters, numbers, and special characters. And consider using a password manager to help you keep track of them all. Enabling multi-factor authentication (MFA) wherever possible is also a good move—it adds an extra layer of security. We’ll give you more details about this in the week 4 blog to help you out.
Keep Software Updated:
Those pesky software updates aren’t just about new features—they often include important security patches. Keep your work devices updated to protect against vulnerabilities that cybercriminals could exploit.
Back Up Your Data:
Regular backups are essential in case of a system failure or ransomware attack. Make sure your data is being backed up securely, so if something goes wrong, you can recover it without losing everything.
Secure Your Devices:
Whether you’re in the office or working remotely, make sure your devices are secure. Lock your screens when you’re away, use strong passwords, and encrypt any sensitive data. Avoid using public Wi-Fi for work tasks unless you’re using a secure connection like a VPN.
Be Careful with Data Sharing:
Think twice before sending sensitive data over email or cloud services. Make sure you’re using secure methods approved by your organization, especially when handling confidential information. Remember, once data is out there, you can’t always take it back.
If You See Something, Say Something
[5] The Department of Homeland Security started this campaign years ago, but the principle applies fully in cybersecurity. Your information security department or IT team will never know as much as you do about what is “normal” in your day-to-day life. If you get an odd email, or you feel like your computer isn’t acting normally, reach out and let somebody know. The time to detect an attack is absolutely critical [6] for your organization, so do your part!
 Cybersecurity Is a Team Effort
Cybersecurity Is a Team Effort
Cybersecurity isn’t just the IT department’s responsibility—it’s a team effort. When everyone is aware of potential threats and knows how to avoid them, we’re much better equipped to protect the organization and the people we serve. In our day-one cybersecurity training for new employees at CaseWorthy, we tell them they’ve been ‘deputized’ to be part of the cybersecurity team. While we’re not looking for any Barney Fife’s to conduct a “Citizen’s arrest!”, the reality is that your team just can’t do this without you.
Regular cybersecurity training is key. Staying informed about the latest threats and learning how to spot them will keep us all safer. If something seems off—whether it’s a strange email or a device acting up—don’t hesitate to speak up. It’s always better to report something and be safe than to ignore it and regret it later.
It’s also important to work together across departments. When the IT team, leadership, and staff collaborate on security policies, we create a more secure environment without disrupting the important work we do. The goal isn’t to make security a burden but to integrate it into our daily routines seamlessly.
Building a Security-First Culture
Creating a culture of cybersecurity awareness is more than just implementing policies—it’s about fostering good habits and open communication. Here’s how we can build a security-first culture together:
Keep the Conversation Going:
Encourage an open dialogue about cybersecurity. If you have questions or concerns, don’t hesitate to bring them up. The more we talk about security, the more aware we’ll be.
Lead by Example:
If you’re in a leadership position, model good cybersecurity practices. When others see that you take security seriously, they’ll be more likely to follow suit.
Stay Updated:
Cyber threats are always evolving. Make sure cybersecurity training and education are ongoing, not just a one-time thing. Regular updates will keep us all informed and prepared for new challenges.
Wrapping Up: You’re Part of the Cybersecurity Solution
Cybersecurity might seem complicated, but it boils down to simple habits and awareness. By staying vigilant, using strong passwords, watching out for phishing scams, keeping your software up to date, and telling somebody if you notice something going on, you’re playing a crucial role in protecting the organization.
Remember, cybersecurity is a team sport, and every role counts. Whether you’re in IT or client services, your actions matter. Let’s all work together to build a safer, more secure environment for our organization and, most importantly, the people we serve.
Your mission is safe with us. See how CaseWorthy prioritizes Security and Compliance.
Sources
[1] https://www.hipaajournal.com/h1-2024-healthcare-data-breach-report/
[2] https://www.secureworld.io/industry-news/unitedhealth-change-healthcare-attack-costs
[3] https://www.b-c-training.com/bulletin/have-cyber-attacks-killed-people-updated-june-2024/

About the Author
Shayne is the CISO at CaseWorthy and a community leader serving as a mentor, trainer, and advocate. He serves on the Chattanooga ISSA board of directors (2017, 2019, & 2021 Chapter of the Year), has been published internationally, served as an examiner for Tennessee’s state National Baldrige Awards, and a mentor for SANS. With over 20 years in cybersecurity, Shayne has built, lead, and/or managed a variety of IT organizations including the Systems Security Officer (SSO) for BlueCross BlueShield of TN’s government business, Sr Prog Mgr. of Power Operations Cyber Security at the Tennessee Valley Authority, Dir of Infosec & Architecture at Erlanger Health System, and CISO at Conversant Group. He has earned professional certifications including GSEC, CISSP, & CISA and an MBA from Bryan College.

 Cybersecurity Is a Team Effort
Cybersecurity Is a Team Effort